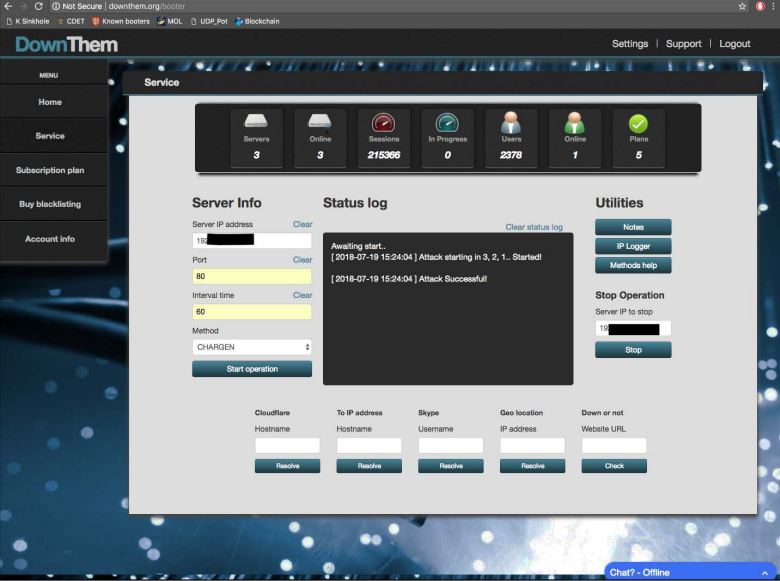
A jury in California today reached a guilty verdict in the trial of Matthew Gatrel, a St. Charles, Ill. man charged in 2018 with operating two online services that allowed paying customers to launch powerful distributed denial-of-service (DDoS) attacks against Internet users and websites. Gatrel’s conviction comes roughly two weeks after his co-conspirator pleaded guilty to criminal charges related to running the services.
Prosecutors for the Central District of California charged Gatrel, 32, and his business partner Juan “Severon” Martinez of Pasadena, Calif. with operating two DDoS-for-hire or “booter” services — downthem[.]org and ampnode[.]com.
Despite admitting to FBI agents that he ran these booter services (and turning over plenty of incriminating evidence in the process), Gatrel opted to take his case to trial, defended the entire time by public defenders. Facing the prospect of a hefty sentence if found guilty at trial, Martinez pleaded guilty on Aug. 26 to one count of unauthorized impairment of a protected computer.
Gatrel was convicted on all three charges of violating the Computer Fraud and Abuse Act, including conspiracy to commit unauthorized impairment of a protected computer, conspiracy to commit wire fraud, and unauthorized impairment of a protected computer.
Investigators say Downthem helped some 2,000 customers launch debilitating digital assaults at more than 200,000 targets, including many government, banking, university and gaming Web sites.
Prosecutors alleged that in addition to running and marketing Downthem, the defendants sold huge, continuously updated lists of Internet addresses tied to devices that could be used by other booter services to make attacks far more powerful and effective. In addition, other booter services also drew firepower and other resources from Ampnode.
Booter and stresser services let customers pick from among a variety of attack methods, but almost universally the most powerful of these methods involves what’s known as a “reflective amplification attack.” In such assaults, the perpetrators leverage unmanaged Domain Name Servers (DNS) or other devices on the Web to create huge traffic floods.
Ideally, DNS servers only provide services to machines within a trusted domain — such as translating an Internet address from a series of numbers into a domain name, like example.com. But DNS reflection attacks rely on consumer and business routers and other devices equipped with DNS servers that are (mis)configured to accept queries from anywhere on the Web.
Attackers can send spoofed DNS queries to these DNS servers, forging the request so that it appears to come from the target’s network. That way, when the DNS servers respond, they reply to the spoofed (target) address.
The bad guys also can amplify a reflective attack by crafting DNS queries so that the responses are much bigger than the requests. For example, an attacker could compose a DNS request of less than 100 bytes, prompting a response that is 60-70 times as large. This “amplification” effect is especially pronounced if the perpetrators query dozens of DNS servers with these spoofed requests simultaneously.
The government charged that Gatrel and Martinez constantly scanned the Internet for these misconfigured devices, and then sold lists of Internet addresses tied to these devices to other booter service operators.
Gatrel’s sentencing is scheduled for January 27, 2022. He faces a statutory maximum sentence of 35 years in federal prison. However, given the outcome of past prosecutions against other booter service operators, it seems unlikely that Gatrel will spend much time in jail.
The case against Gatrel and Martinez was brought as part of a widespread crackdown on booter services in Dec. 2018, when the FBI joined with law enforcement partners overseas to seize 15 different booter service domains.
Federal prosecutors and DDoS experts interviewed at the time said the operation had three main goals: To educate people that hiring DDoS attacks is illegal, to destabilize the flourishing booter industry, and to ultimately reduce demand for booter services.
The jury is still out on whether any of those goals have been achieved with lasting effect.
The original complaint against Gatrel and Martinez is here (PDF).